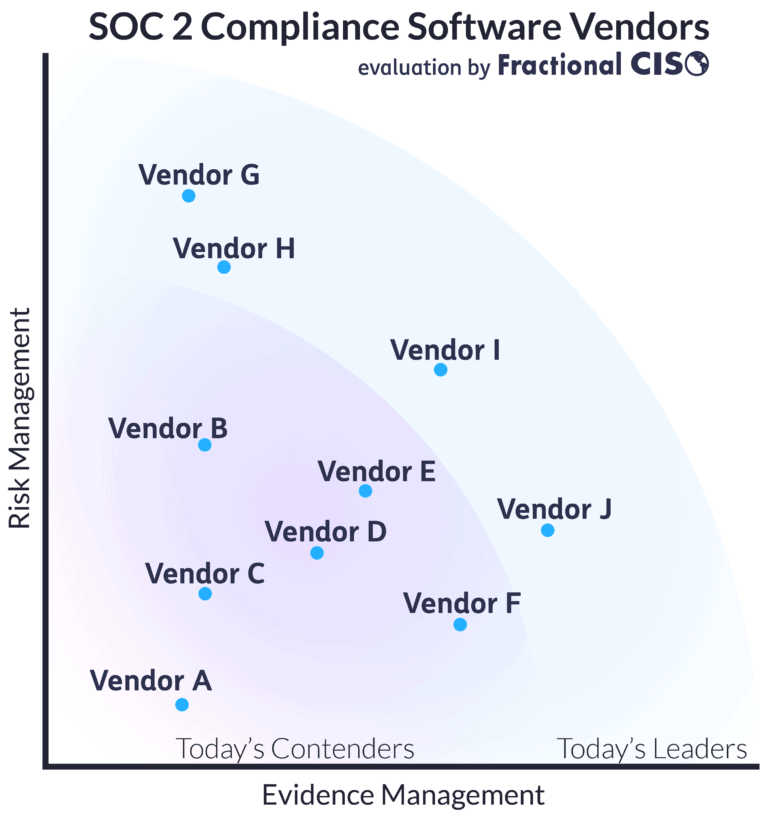
We compared 10 SOC 2 compliance software vendors to see who’s leading this quickly-growing market.
Introduction
Many of Fractional CISO’s clients have asked us which SOC 2 compliance software vendor they should select to help them run their SOC 2 program. This paper explorers the answer which is… it depends!
Many cybersecurity compliance tools hit the market over the last few years, largely due to increasing market pressure for companies to improve their cybersecurity posture. In the United States specifically, large enterprises are frequently looking for their vendors to have an AICPA SOC 2 attestation report. Getting ready for a SOC 2 audit takes a lot of work, so midsize companies are looking for tools to make the job easier.
To make things easier for the prospective customers of these vendors, Fractional CISO has evaluated 15 available services and created this white paper evaluating them.
This paper explores 10 of the 15 evaluated vendors based on the criteria for inclusion. Each vendor’s offering is examined, discussed, and ranked as either one of today’s leaders or today’s contenders in this space.
Evaluated SOC 2 Compliance Software Vendors
Fractional CISO evaluated the following vendors:
- – Drata
- – JupiterOne
- – LogicGate Risk Cloud
- – Ostendio MyVCM
- – Shujinko AuditX
- – Secureframe
- – Strike Graph
- – Tugboat Logic
- – Vanta
- – ZenGRC by Reciprocity
Criteria for Inclusion
In order to be included for evaluation, SOC 2 compliance software vendors must meet the following criteria:
- 1. Provide software designed for SOC 2 compliance.
- 2. Have their own SOC 2 attestation.
- 3. Sell a product that’s suitable for midsize companies.
- 4. Have service that includes pre-written policies.
- 5. Provides evidence management capabilities.
Fractional CISO also investigated the following vendors, but excluded them:
- – Apptega: does not have a SOC 2
- – HyperProof: does not provide pre-built policies
- – KnowBe4 GRC: does not provide pre-built policies
- – Securicy: does not have a SOC 2. They are on-track to receive one soon.
- – Orca Security: is not really a compliance tool – could be combined with any of the evaluated tools given a more in-depth review in the paper.
Additionally, the following vendors appear to meet the criteria but Fractional CISO learned of them too late to be included in the paper:
- – Laika
- – LogicManager
- – ByteChek
- – ControlMap
- – Control by Very Good Security
- – Anecdotes
Where a Platform Can Help
There are a number of areas that a platform can assist a company in preparing for a SOC 2 audit:
- 1. Expert guidance through the SOC 2 process
- 2. Strong tie to SOC 2 Control set
- 3. Templates for Policies and Procedures
- 4. Good workflow for interacting with the auditor
- 5. Evidence Management
- 6. Automated Evidence Collection
- 7. Risk Management
- 8. Vendor Risk Management and evaluation
- 9. Re-use content for other frameworks
Two Areas of Focus: Evidence Management and Risk Management
Vendors were evaluated on two primary areas that they provide assistance: evidence management and risk management.
Evidence management helps facilitate the evidence-gathering process of SOC 2 preparation. Countless services are needed to run a modern business, email and office providers like Google Workspace and Microsoft 365, cloud computing from Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure, and project management from Atlassian are just scratching the surface – and they’re all likely to hold sensitive data. Good evidence management helps in many ways – does the tool offer the ability to automatically collect, analyze, and facilitate human review of evidence? Can the tool easily share evidence with the auditor? Is there a workflow that allows for managing evidence across multiple years of SOC 2 audits? Generally, services that provide more functionality and more integrations ranked higher in this area.
When selecting a SOC 2 compliance software vendor, it’s vital to pick one that supports whatever services you use – or could see yourself using.
Risk management covers risk assessments, vendor risk management, and providing guidance for risk reduction activities. SOC 2 compliance software vendors can make the risk management process easier by generating pre-built policies, performing risk assessments (ideally audit-ready), and performing vendor management – including generating vendor questionnaires. Generally, compliance software vendors scored higher in this area for having mature tools that provide more functionality.
All of these tools will help you get a SOC 2, but some will save you more time than others and offer additional features and specializations you may benefit from.
Chart and Analysis
After evaluating each company, we grouped them as today’s leaders and today’s contenders. “Today’s” is an important part of this judgment. The SOC 2 compliance software market is both young and dynamic. Like most SaaS vendors today, the vendors covered in this paper are constantly updating their products with tweaks, patches, and new functionality. It is very possible for any of these companies to quickly develop their tools or to stagnate while others leap ahead.
To download a copy of the complete white paper, sign up for our cybersecurity newsletter for business leaders, Tales from the Click.
The full white paper includes:
- – A non-anonymized chart with ranking for each vendor
- – Strengths and weaknesses in analysis for each vendor
- – Appendix with vendors’ supported compliance frameworks and service integrations
Sample content continues after the form.
Drata
Drata is one of today’s leaders in SOC 2 compliance software. Drata is heavily focused on automation, providing a strong system capable of collecting large amounts of evidence automatically and generating an inventory of cyber assets your company is using. Drata’s integrations are largely powered by APIs, but Drata also provides an agent for customers without an MDM solution.
Suitably, Drata provides many different vendor integrations and can automate many controls in each vendor.
Product Strengths and Product Weaknesses available in full white paper.
Drata was founded by Adam Markowitz, Daniel Marashlian, and Troy Markowitz in 2020. They are located in San Diego and have about 45 employees.
JupiterOne
Even though it isn’t positioned as SOC 2 compliance software, JupiterOne does play in this space. JupiterOne is actually positioned as a cyber asset management and governance platform, but it meets Fractional CISO’s criteria for this review and can be used for compliance.
JupiterOne provides the most vendor integrations and very powerful automated evidence collection tools. After integrating JupiterOne and letting it scan all your systems, it creates a spider graph to visualize how everything is connected – creating a map of a company’s digital infrastructure and the relationships between each component.
However, JupiterOne’s comes up short when using that data for SOC 2 compliance, it’s lacking in risk management functionality and doesn’t provide great compliance workflows. While the program is capable of helping a company on its compliance journey, JupiterOne is more focused on IT and cybersecurity.
Product Strengths and Product Weaknesses available in full white paper.
JupiterOne was founded in 2018 by Erkang Zheng. They currently have around 60 employees and are headquartered in Morrisville, North Carolina.
LogicGate Risk Cloud
LogicGate’s software service is called “Risk Cloud” and as the name implies, it is especially focused on risk management.
Risk Cloud has four different modules for general risk assessment/management and three specialized modules for vendor risk management. These modules are mature, well-designed, and cover a wide array of risk management needs.
Risk Cloud has little capacity for evidence collection. In fact, most of it is not automated, instead requiring manual uploading of evidence. Once uploaded, the system will retain the information and continuously refer back to evidence and integrations to update risk assessment information.
Product Strengths and Product Weaknesses available in full white paper.
LogicGate was founded in 2015 by Dan Campbell, Jon Siegler, and CEO Matt Kunkel. They are located in the Greater Chicago Area and currently have about 190 employees.
Ostendio MyVCM
The Ostendio MyVCM service is aimed at helping companies create and run their security programs as a whole, not just enabling SOC 2 compliance.
Ostendio offers powerful tools for uploading, tagging, and distributing evidence. MyVCM also has a unique module for vendors to connect with. Ostendio customers invite their vendors to access a lite version of the MyVCM platform, where they will complete risk questionnaires and provide compliance evidence. Ostendio recognizes leading vendors in its monthly MyVCM Trust Network awards to highlight vendors with great cybersecurity programs connected to its tools.
Product Strengths and Product Weaknesses available in full white paper.
Ostendio was founded in 2013 by Vidit Mittal, Jermaine Jones, and Grant Elliot. Ostendio has about 40 employees.
Shujinko AuditX
Shujinko AuditX is designed to be a system of record for security audits. Once evidence is uploaded for one audit framework, it can easily be transferred to another.
AuditX’s user experience is designed around audits. The user creates an “audit” with a framework of their choice, and a dashboard is created with controls mapped to the selected framework. Each control has lists of evidence that Shujinko suggests including for compliance.
Unfortunately, Shujinko’s automation and risk management systems are very limited. Evidence collection will pull documentation from the linked vendor, but the evidence will require manual review to ensure compliance – nothing is automatically flagged.
Shujinko will likely be very appealing to a large number of companies for SOC 2 due to its pricing: free. Shujinko does charge a fee for any frameworks besides SOC 2.
Product Strengths and Product Weaknesses available in full white paper.
Shujinko was founded by Scott Schwan and Matt Wells in 2018. It has about 30 employees and is based in Seattle, Washington.
Secureframe
Secureframe’s service aims to streamline the SOC 2 process. After signing up, customers will first link all of their cloud accounts and add all of their employees to Secureframe. Secureframe will perform automatic scans on all integrated accounts to check to flag vulnerabilities and incorrect security configurations. It aims to streamline the preparation process by using this data to create checklists of tasks needed to get an organization ready for the audit.
In addition to the compliance software itself, Secureframe provides a customer success manager and a compliance expert to help client companies prepare for an audit.
Product Strengths and Product Weaknesses available in full white paper.
Secureframe was founded in 2020 by Natasja Nielsen and Shrav Mehta. It’s located in San Francisco (and Denver) and has about 40 employees. In addition to its SOC 2, Secureframe has an ISO 27001 certification.
Strike Graph
Strike Graph combines both its tool and customer success representatives to guide its clients to SOC 2 compliance and provides a continuous living record of compliance activities.
Strike Graph’s user experience starts with a risk assessment process. Strike Graph personnel will work with the company to move through the manual risk assessment tool to create a control library. Each control in the library is mapped to the SOC 2 criteria, and each control will request the policies and evidence needed to bring it into compliance.
A special, unique feature that Strike Graph provides is an automated security questionnaire responder. Clients can upload one of their customer’s questionnaires, and Strike Graph’s algorithm will complete it automatically.
Product Strengths and Product Weaknesses available in full white paper.
Strike Graph was founded by Justin Beals and Brian Bero in 2020. Located in Seattle, it is the most recent company on this list to have entered the market. Strike Graph has approximately 25 employees.
Tugboat Logic
Tugboat Logic is one of the strongest solutions for overall compliance audit preparation and management but doesn’t excel in evidence management or risk assessment.
Its automated evidence collection tools feature many integrations and have multiple use cases, including code review, access management, security awareness training, endpoint protection, and more.
Its vendor risk management system is also mature, providing users with pre-built security questionnaires for vendors or allowing them to create their own. Questionnaires are completed in Tugboat Logic’s online portal and stored in one location.
Tugboat Logic also has a strong risk management system that allows for mitigating controls to be mapped to the SOC 2 framework. Product Strengths and Product Weaknesses available in full white paper.
Tugboat Logic was founded by Ingrum Putz and CEO Ray Kruck in 2017 and boasts about 120 employees. It’s located in Burlingame, California, and has an ISO 27001 certification in addition to its SOC 2.
Vanta
Vanta is one of today’s contenders in SOC 2 compliance software. Vanta is focused on automation and uses API-based integrations and the optional Vanta Agent to collect evidence from endpoints, servers, and other software services to ensure compliance.
Evidence from integrations is automatically collected and uploaded to a dashboard that creates a checklist of compliance activities needed to get ready for the audit. This checklist helps to streamline the process of preparing for the audit.
Product Strengths and Product Weaknesses available in full white paper.
Vanta was founded by Christina Cacioppo and Erik Goldman in 2017. Vanta currently has about 100 employees and is headquartered in San Francisco.
ZenGRC by Reciprocity
As the “GRC” in the name implies, ZenGRC is focused on being a one-stop shop for risk management and compliance.
ZenGRC uses a system of record to collect and apply evidence to multiple audit frameworks. It supports SOC 2 but is not focused exclusively on it. Instead, Reciprocity’s ZenGRC aims to be a central hub for all sorts of audit frameworks. The tool makes it easy to move from one framework to another.
It has a mature set of risk management and evidence collection tools. ZenGRC doesn’t integrate with quite as many services as other vendors discussed in this paper do, but an open API can be used for other, non-direct integrations.
Product Strengths and Product Weaknesses available in full white paper.
Reciprocity was founded by Ken Lynch in 2009. They are headquartered in San Francisco. They currently have approximately 130 employees.
Conclusion
Demand for security-compliant vendors is growing quickly, creating an increased demand for resources that help companies become compliant. It’s no wonder that so many companies have created SOC 2 compliance software vendors to help fit that growing need.
All of the tools discussed here will make SOC 2 compliance easier for your company, but some will do it better than others. We recommend selecting two or three from this list and receiving demos for yourself before making a final decision.
To download the complete white paper and get all of the information to help you make your decision, sign up for our newsletter at the form above!
Our monthly newsletter, Tales from the Click, provides free and actionable cybersecurity advice for business leaders. The advice in each newsletter will help you build your security program and become compliant!