Cyber Security News and Articles
CMMC Rulemaking Updates: 7 Things You Need to Know
The Department of Defense officially submitted the CMMC 2.0 rule to the Office of Information and Regulatory Affairs (OIRA), under the Office of Management and Budget (OMB). Here's what you need to know about the latest CMMC update. The Department of Defense (DoD)...
MGM Resorts International was hacked via a social engineering campaign
Earlier this week MGM Resorts International was hacked via a social engineering campaign. Senior Manager of our Penetration Testing practice, Erik Dominguez, joined us to share his thoughts on how it happened, what it means, and what companies should be doing to make...
CMMC: Its Importance and Impact on Organizations
What is CMMC? Initiated by the United States Department of Defense (DoD), the Cybersecurity Maturity Model Certification (CMMC) is a framework designed to measure the cybersecurity maturity level and align processes and practices with the type and sensitivity of the...
The 10 Biggest Risks And Threats For Businesses In 2022
Risks and threats are precursors to corporate crisis situations. Some risks are universal, and pose a threat to every company, while other are relative and depend on the nature of an organization’s business or industry. No matter which risks or threats apply to a...
5 Common Computer Security Threats Businesses Are Facing in 2022
Do you want to keep your office secured and defended against a virus? What do you think are the main threats to an office’s computer security? Many of us don’t lock our offices at home at night, no matter how many notifications pop up. There are several threats to...
Everything and Anything You Need To Know About SOC 2
Protecting customers' data is a concern for all organizations regardless of the industry or size. Most organizations outsource key aspects of their business to third-party vendors such as Software-as-a-Service (SaaS) solutions or cloud hosting providers (i.e. Amazon...
What does the SOC2 Report cover?
Businesses often outsource services related to information technology and cloud services to the third-party for better operations. Although outsourcing may be a convenient option, yet it cannot possibly work smoothly without checks and due diligence. Entrusting your...
What to Know About Emerging SOC 2 Compliance Software: Part 1
The number of new software options that promise to streamline SOC 2 compliance has exploded in recent years – but are they really making compliance easier? There is no magic answer, but while SOC 2 compliance software can help you get a better understanding of...
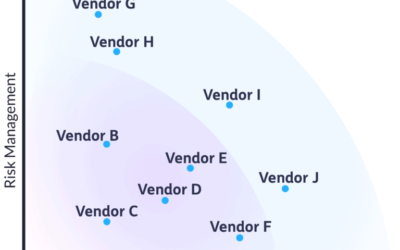
Comparing SOC 2 Compliance Software Vendors
We compared 10 SOC 2 compliance software vendors to see who’s leading this quickly-growing market. Introduction Many of Fractional CISO’s clients have asked us which SOC 2 compliance software vendor they should select to help them run their SOC 2 program. This...
The Defense Department recently streamlined its Cybersecurity Maturity Model Certification program.
The Defense Department recently streamlined its Cybersecurity Maturity Model Certification program. As 2022 dawns, the Defense Department is hoping for a smoother path ahead for its process of ensuring that all defense industrial base contractors meet cybersecurity...